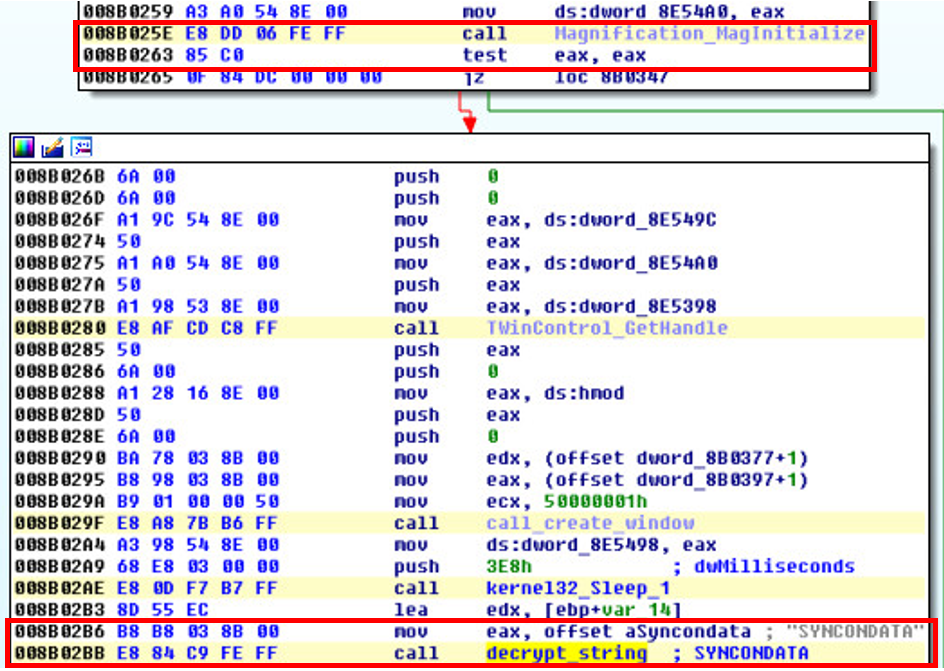
Taking Over the Overlay: What Triggers the AVLay Remote Access Trojan (RAT)? - Malware Analysis - Malware Analysis, News and Indicators
This is the second installment in a three-part series on the AVLay RAT discovered by IBM X-Force. Part one explained how the researchers reverse engineered the malware. The third installment will demonstrate how X-Force gained control of AVLay and fully simulated the overlay attack in its labs. Most overlay malware attacks work in similar ways. To begin, the malware monitors active browser windows the user is interacting with, waiting to match a window caption or class name with those on its ta
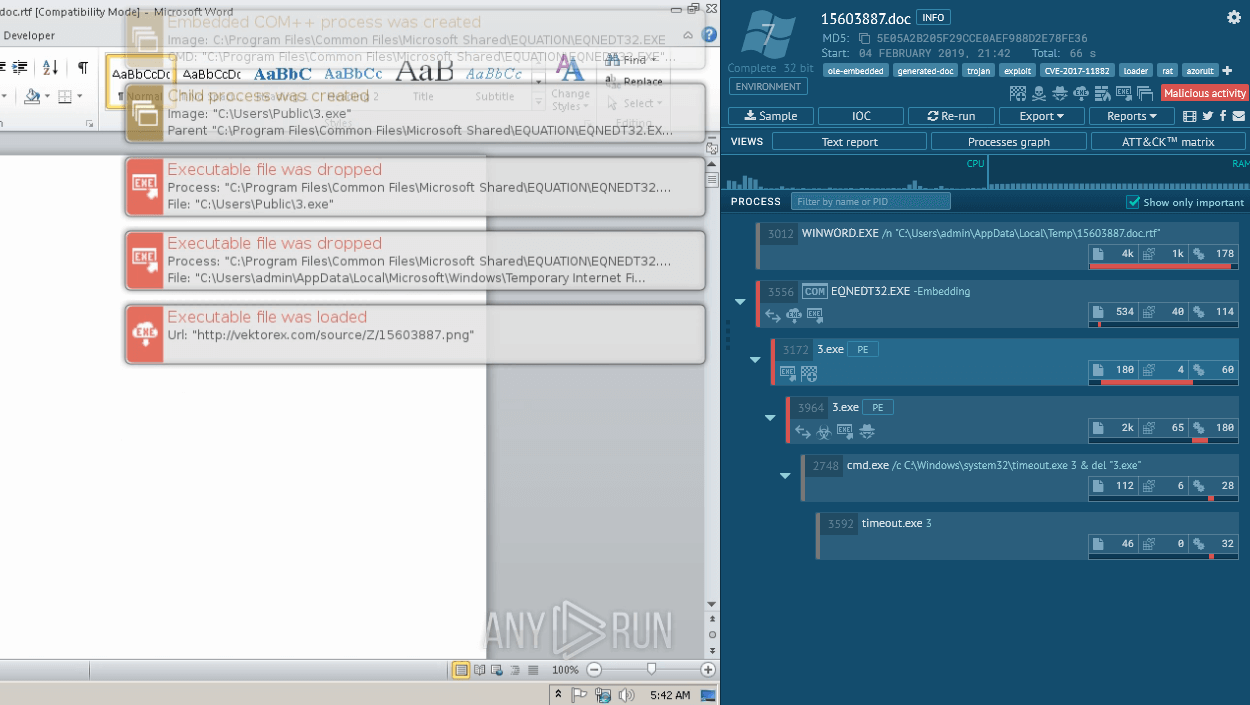
AsyncRAT Malware Analysis, Overview by

RATs Race: Detecting remote access tools beyond pattern-based

RATs Race: Detecting remote access tools beyond pattern-based
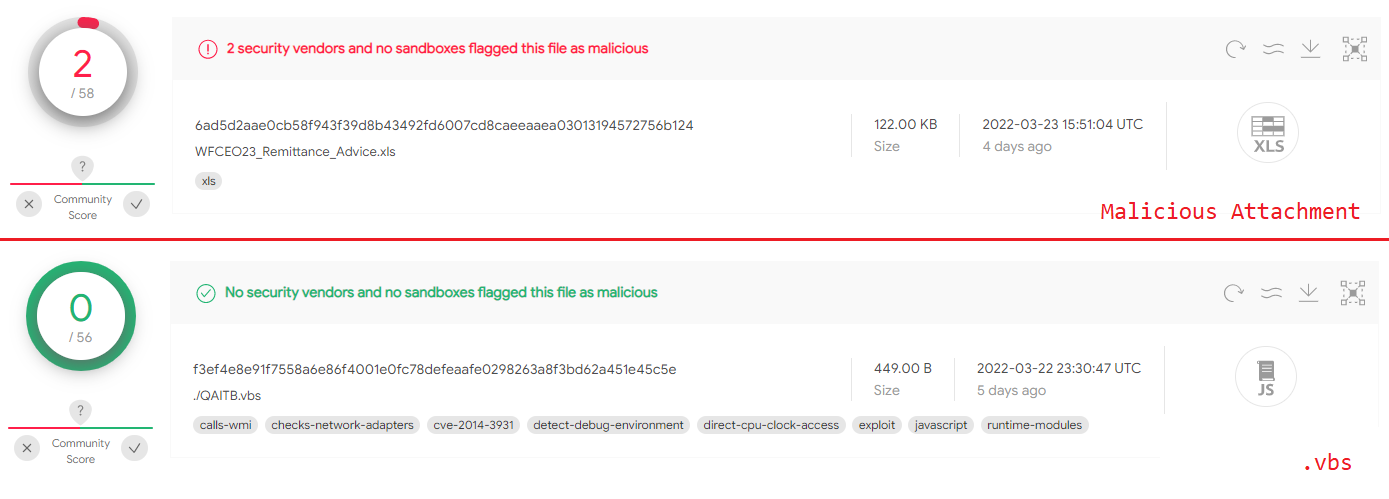
Remcos Trojan: Analyzing the Attack Chain
Orcus RAT Technical Malware Analysis and Configuration Extraction

What is Remote Access Trojan (RAT)? - Check Point Software
Taking Over the Overlay: Reconstructing a Brazilian Remote Access

Taking Over the Overlay: What Triggers the AVLay Remote Access

RAT - Remote Access Trojan - Stats, Details, and What to Know









