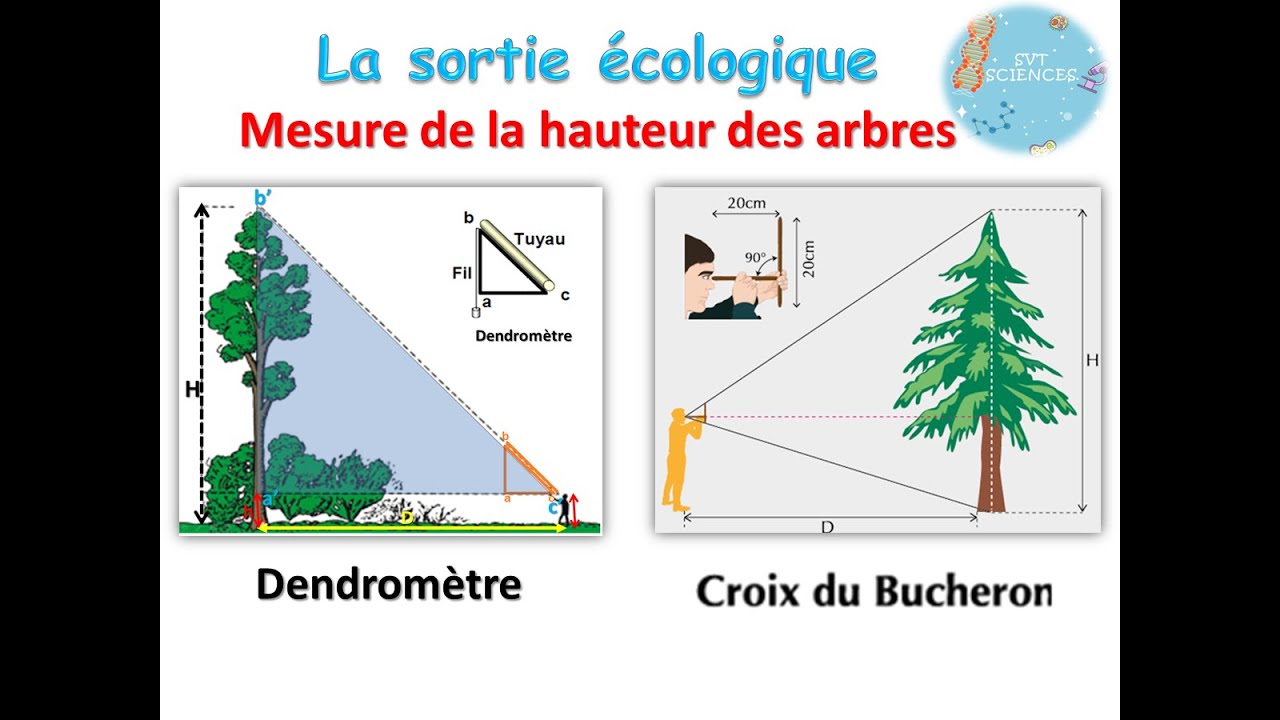
A Deep Dive into Windows Hello (2) - Hackers In inTrusion Laboratory
Client-side Login Procedures With protocol analysis, we figure out what data is exchanged between the client and the server for Windows Hello login. Now we’d like to know where is authentication data stored in the client-side? And how authentication data is used to? For these, we performed static and dynamic debugging for login-related services on … Continue reading A Deep Dive into Windows Hello (2) →
ULTIMATE HACKER SUMMER CAMP — Part Five: DEFCON Safe Mode, by DCG 201

CSCI369 Lab 2, PDF, Transmission Control Protocol

A Deep Dive into Windows Hello (2) - Hackers In inTrusion Laboratory

A Deep Dive into Windows Hello (2) - Hackers In inTrusion Laboratory

Building an RDP Credential Catcher for Threat Intelligence, NCC Group Research Blog

Bypassing Windows Hello Without Masks or Plastic Surgery

A Deep Dive into Windows Hello (2) - Hackers In inTrusion Laboratory

New 0-Day Attack Targeting Windows Users With Microsoft Offi - vulnerability database

A Deep Dive into Windows Hello (2) - Hackers In inTrusion Laboratory

This Researcher Hacked Windows Hello Using the Ultimate in Public Data: Your Face

Computer Systems Security: Planning for Success
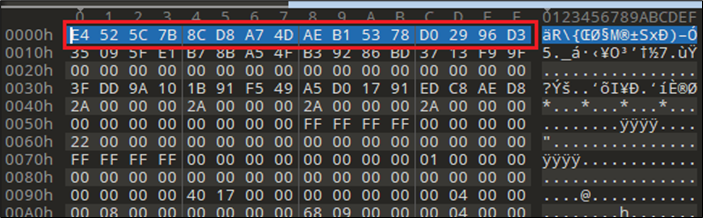
The Rising Trend of OneNote Documents for Malware delivery

A Deep Dive into Windows Hello (2) - Hackers In inTrusion Laboratory